Vulnerability Management
Lifecycle Support
Our Vulnerability Management Lifecycle (VML) support service provides an end-to-end process that articulates actionable insight and discovery of critical vulnerabilities within the crevices of applications and systems.
Vulnerability Management Lifecycle Support
Vulnerability Management (VM) is the process of identifying, prioritizing, remediating, and reporting vulnerabilities – weaknesses that reduce the protection of integrity, availability, authenticity, non-repudiation, and confidentiality. VM depends on configuration, change, asset, and network security to manage vulnerabilities. With the ever-increasing number of malware, applications, systems, cloud, and configuration deficiencies, most organizations are stranded in managing vulnerabilities. Legacy programs exist, and security approaches change over time and can produce risks when vulnerabilities age. A modernized VML is a continuous engagement that seeks to mitigate or remediate vulnerabilities before cyberattackers cause damage.
Our Structure for a VML
The VM program directly relates to various IT disciplines, commonly called workstreams. These disciplines communicate business needs, organizational risks, system identification, and reporting requirements for the VM program. Each workstream aligns with an available VM program's people, process, and technology integration. Considering the complex nature of aligning all three components, it can cause severe over lapse and affect security readiness. We have developed a more streamlined practice where our VML integrates all phases of a VM program and simplifies the remediation process.
Prework for Vulnerability Management
Determine scope
of program

Define roles and
responsibilities

Select vulnerability
assessment tools

Create and refine policy
and SLAs

Identify asset context sources
Vulnerability Management Lifecycle Process
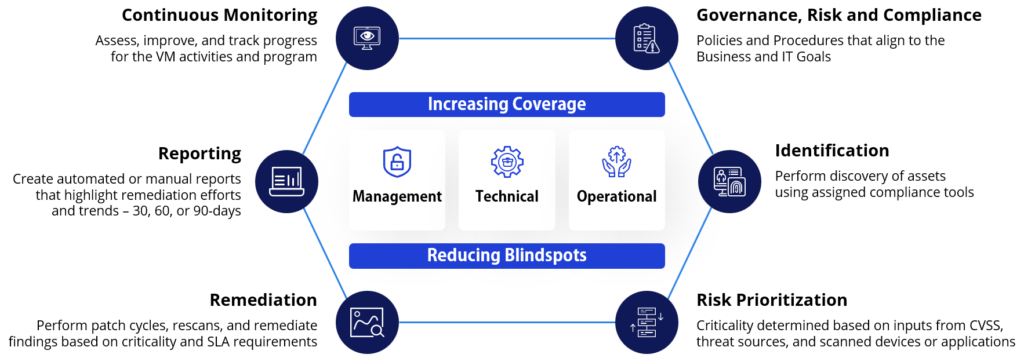
Through our lifecycle services, we can perform hygiene requirements to identify areas of improvement. The process incorporates several workstreams and vulnerability management governance strategies to reduce program deficiencies. We perform a Current State Analysis to define the state and recommendations that require maturity. Onboarding our lifecycle program reduces future risks, drives coverage and risk reduction, and makes IT systems environments more secure and resilient.
What Does Our VML Advisory Service Provide
The most mature cyber organization has discovered themselves unable to develop an end-to-end vulnerability management program. This is where SEMAIS can support in modeling and implementing a VML that supports security visibility, risk reduction, and increased protection by:
Assessing a Configuration Database (CMDB) to identify and report missing or inaccurate assets
Supporting the design of a RACI chart to outline roles and responsibilities
Developing APIs to integrate tools such as ServiceNow, BigFix, Tenable, or PowerBI

Providing and identifying threats to specific platforms and applications
Prioritizing risks based on CVSS, threat intelligence, severities, and scanned inputs
Connecting the VML program to Incident Response, Penetration Testing, GRC, ITSM, and other cybersecurity programs
Assisting with designing and engineering compliance scanner and connected tools
Developing and managing backlog and burndown campaigns for vulnerabilities
Creating scan schedules and target groups for assets and software under scope.

Delivering status reports that highlight trending over a specific time – 30, 60, 90 days

Integrating workstream solutions into a VML and its operations
Our Workstream Process for Vulnerability Management
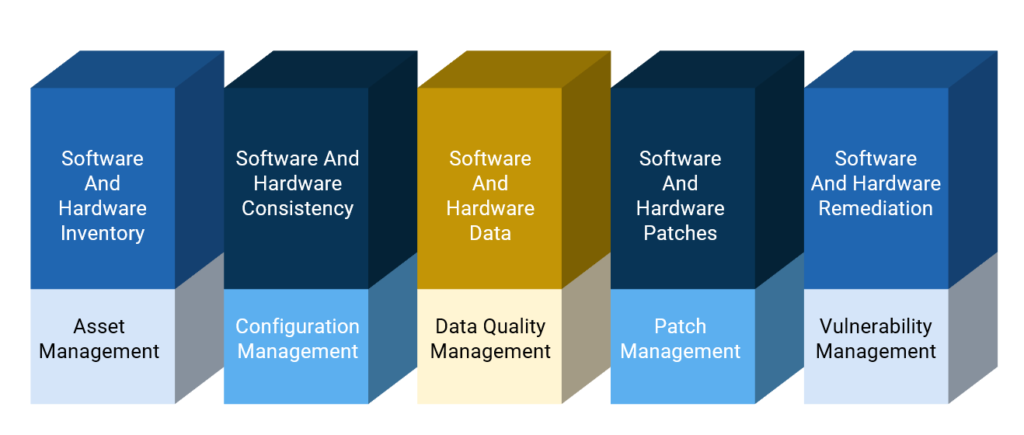
Semais Solution for Vulnerability Management
We deploy an actionable Vulnerability Management process that clients can use to identify, prioritize, and remediate information technology (IT) vulnerabilities, weaknesses, or exposures. Organizations can create additional challenges and prolong remediation cycles without the proper skills to develop an end-to-end process. Combing the outcome with failing patch management schedules, inaccurate inventory counts, or inaccurate metrics can compromise an enterprise. Our Vulnerability Lifecycle Support Service and its infrastructure components can mitigate these risks.

Authentication and Configuration Auditing

Reconnaissance, Scanning, and Vulnerability Fundamentals

Remediation Concepts and Vulnerability Assessment Reporting

Vulnerability Assessment Methodology

System Profile and Discovery of Assets

Tool Configuration and Scanning Procedures

Security Patch and Remediation

Prioritization of Vulnerabilities