Cybersecurity Assess & Authorization
We help clients gain security visibility and control into internal and external risks that impact the federal and DoD architects.
Risk Management Framework (RMF)
We are familiar with the security authorization process and the Risk Management Framework (RMF) from NIST Special Publication (SP) 800-37. This includes conducting the activities of security categorization, security control selection and implementation, security control assessment, information system authorization, and security control monitoring. We ensure that information system-related security risks are consistent with the government mission/business objectives and that the overall risk strategy supports consistent, well-informed security authorization decisions throughout the information system lifecycle.
SEMAIS Approach to RMF
We approach Risk responsibly to eliminate security gaps and drive protection standards that defend the most critical applications, data, and infrastructure devices. This service transitions into the government security authorization process. We use security indicators to improve reporting, monitoring, and risk mitigation. These indicators enable clients to forecast operational tasks and identify risks or potential losses before their occurrence. We provide metrics and gap analysis by utilizing automated tools: eMass, RiskVision, CSAM, HBSS, IBM BigFix, Fortify, ACAS, Nessus, and Splunk that enable 360 degrees of security visibility.
Road Mapping Cybersecurity
We help clients gain security visibility and control into internal and external risks that impact the federal and DoD architects. Our approach ensures that effective risk management programs create value and are tailored to system and agency's specifications; and engages cybersecurity as a continual improvement and enhancement.

Driving Cybersecurity Outcomes
Our RMF Assessment and Authorization (A&A) process provides a structured, yet flexible approach for managing the portion of risk resulting from the incorporation of information systems into the mission and business processes of hte organization; and processes to help agencies pass FISMA, CCRI Inspections, and OIG Audits.
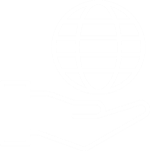
RMF Methodology
SEMAIS Automated A&A Approach
Follows the NIST RMF Six-Steps and
Provides Key Reliabilities
Real-time risk management and ongoing information system authorization through the implementation of robust continuous monitoring processes.

Automated process for selecting, implementing, assessing, and monitoring security controls, and authorizing information systems.

Information to senior leadership needed for cost-effective, risk-based decisions regarding the organizational information systems supporting their core missions and business functions.
Responsibility and accountability process for security controls deployed within organizational information systems and inherited (i.e., Common Controls) by those systems.

Integrated information security process into the enterprise architecture and system development life cycle.

Automated import and mapping capability for vulnerability assessment and system event data.

Accurate Security Authorization Packages through the standardization of A&A process and documentation.
