Digital Modernization
The current security landscape has many challenges and legacy applications that are not cybersecurity ready. These aging systems and outdated business drivers can accelerate risks and cause security gaps across many platforms. Many initiatives and approaches seem aligned, but having an advanced "security eye" can reach a much more comprehensive view and accelerate successful modernization.
The DoD published its Modernization Plan in 2019 and the involvement has shaped the government's attention to revisit security and make better decisions. The commercial market has also taken strides and onboarded similar technologies and a DoD's philosophy into modernizing IT systems and resources.
Digital Modernization 101
Digital modernization is the process of upgrading or adopting new business-enabling technologies (e.g., cloud services, email and collaboration platforms, and critical systems such as enterprise resource planning (ERP), Electronic Health Records, Robotic Surgeries, Voice-Activated systems for health communication, logistics, and human resources to improve existing processes, achieve new efficiencies, and reduce costs. The core has enabled cloud technologies, artificial intelligence, zero-trust, and threat intelligence platforms to advance data access and analysis for security initiatives.
Technology is a Changing Landscape and Security Engagements Must Advance
The security landscape integrates many uncertainties and architectural challenges as technology and threats advance. Continuous use of legacy systems and stagnant business services can defeat the premises of cybersecurity – increasing protection and lowering risk. The outcome can adversely affect security growth and compliance. When viewing modernization across platforms and diverse technology portfolios, it's agreeable that a holistic security approach enables digital modernization and transformation. This is where organizations must consider the entire landscape and current technologies for application, cloud, data, infrastructure, and networking, and "Rethink Their Engagement Strategy."
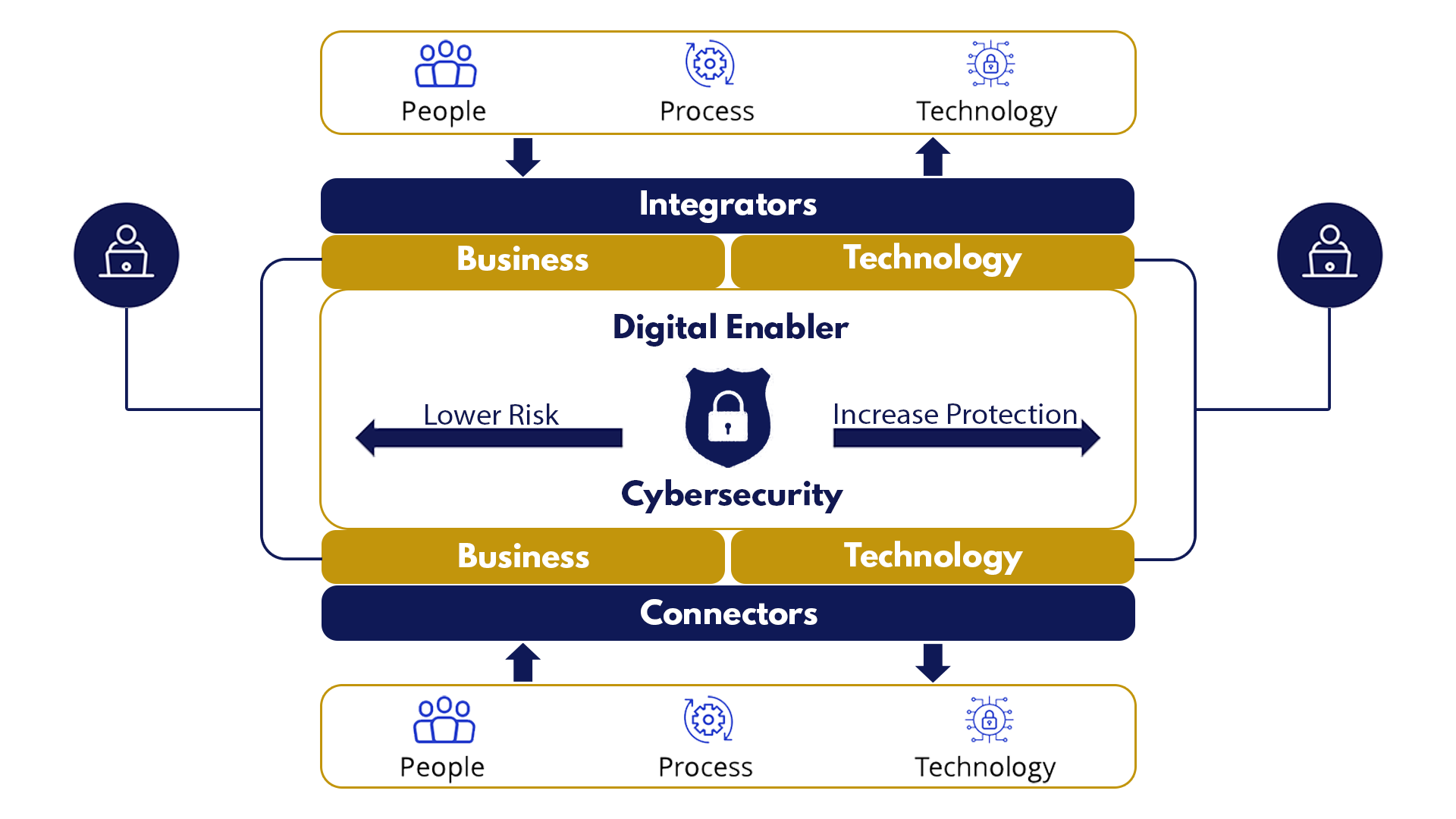
Our Solution for Digital Modernization
Our digital advancement solution involves an end-to-end process that increases protection, lowers risks; and sustains operations and productivity. We use enablers that segment the strategy into success points – it defines each enabler and considers tradeoffs, return-on-investment, technology innovations, connectors, and security integration. This strategy provides a more realistic view that makes the engagement viable. To drive the approach, we isolate the change process into three critical steps: defining the target state for cybersecurity, deciding which landscape component needs refinement – people, process, or technologies, and determining the implementation process. A typical engagement may involve risk prioritization schemes that optimize vulnerability remediation timelines and data aggregation. Digital modernization tools that support AI or Cloud services are then considered, and for business transformation, we would assess requirement gathering and performance factors.

The cybersecurity industry has adopted many standards and digital modernization strategies. These standards require in-depth interpretation and sound solutions to ensure compliance.

Data breaches, system intrusions, data protection, and information protection schemes are risk-prone, which requires organizations to stay ahead and eliminate risks.

Internal security assessments provide normal insight into security deficiencies. An external advisor can provide a more in-depth and unbiased evaluation.

The privacy laws are changing, and security best practices are sometimes omitted from governance strategies, and a trusted advisor is needed to bridge security.

Organizations operate adhoc to sustain vulnerability management, security tool integration, cyber hygiene requirements, and continuous risk monitoring service.






