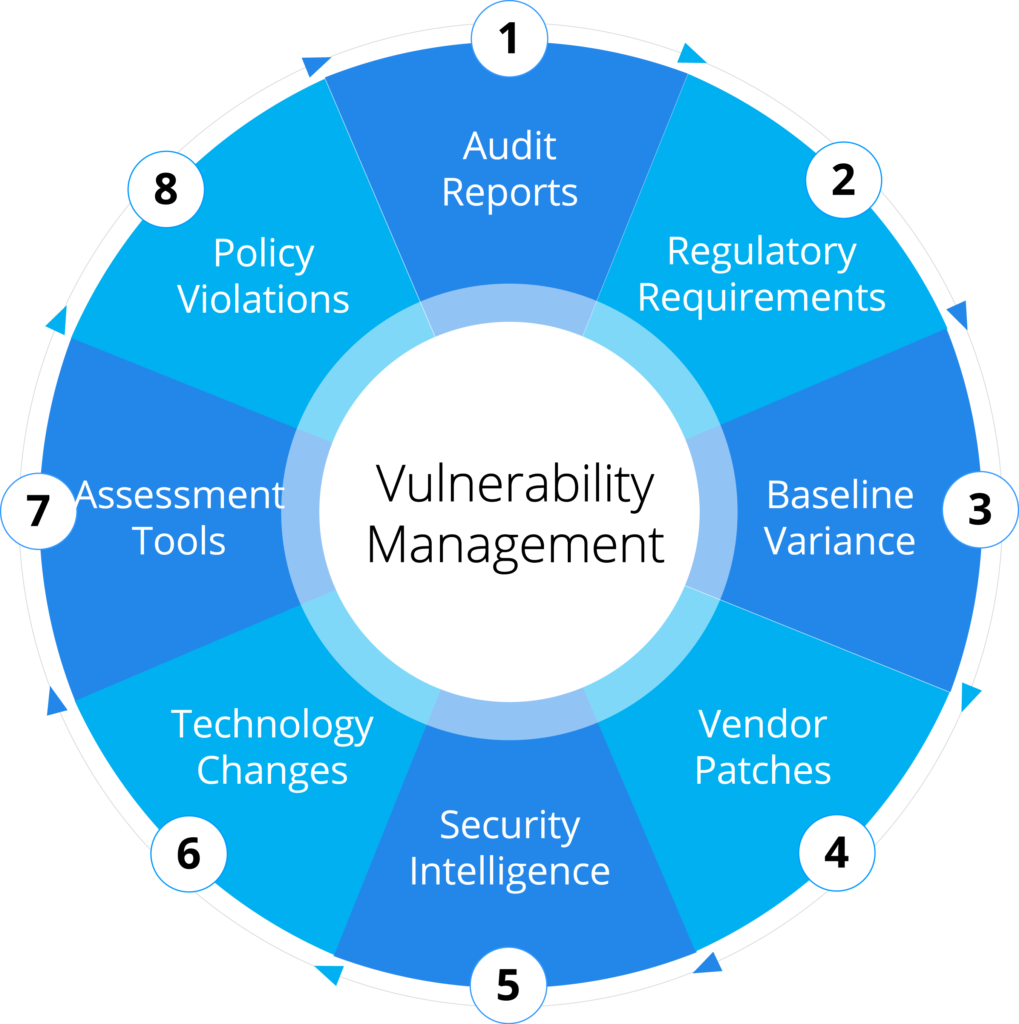
Vulnerability Management
Our data collection demonstrates the actual costs of fixing security problems after they have been introduced.
Organizations can make informed decisions; prioritize remediation efforts, and integrate security into the application and system development lifecycle for future remediation.
We leverage a comprehensive process that tracks root cause across Software Assurance (SwA), 3rd Party Applications, Baseline Changes, Assessments, or Network Infrastructure components that become vulnerable.
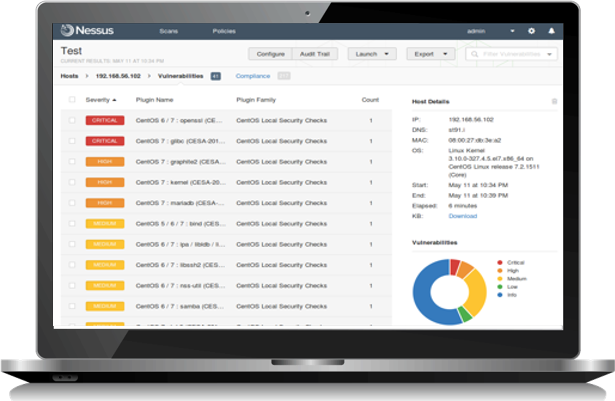
01. Prioritize flaws, strengthen resistance to attacks
Prioritize the remediation of flaws with and without CVEs (misconfigurations, default passwords, weak permissions) with the use of attack correlation, intelligence sources and the integration with the CIS Benchmarks and U.S. Department of Defense System Agency's Security Technical Implementation Guides.

02. Reduce stress and shorten remediation times
A concurrent remediation model helps make the process manageable no matter the size of your team. The most critical vulnerabilities are sent to remediators and, once they are fixed, the next batch arrives.

03. Maintain regulatory compliance
Vulnerability management helps you comply with data protection mandates in regulations such a the GDPR, HIPAA and PCI DSS and avoid teh significant impact of penalities and demage to your reputation.
Innovative Solutions to move vulnerability programs forward
Without the proper skills to develop a remediation strategy and decide what vulnerabilities are a priority can create additional challenges and prolong remediation cycles. Combing this risk with failing patch management schedules, inaccurate inventory counts, or unrealistic metrics can compromise your enterprise. Our Vulnerability Lifecycle Support Service can mitigate these risks.

Authentication and Configuration Auditing

Reconnaissance, Scanning, and Vulnerability Fundamentals

Remediation Concepts and Vulnerability Assessment Reporting

Vulnerability Assessment Methodology

System Profile and Discovery of Assets

Tool Configuration and Scanning Procedures

Security Patch and Remediation

Prioritization of Vulnerabilities
Continuous Risk Monitoring
Most attacks today incorporate multiple steps, crossing different vectors (Network, Web, Mobile, Wireless, Endpoint). An isolated view of these steps could appear harmless – causing a potentially drastic oversight. We use “System Thinking” to drive the most successful VuMP process.
Our security visibility process examines the IT architect through discovery and credential scanning, and asset profile reports.
We utilize effective AI tools and processes that drive remediation and reporting across the entire IT architect.
Organizations can identify failing patch levels, misconfiguration issues , rogue or unauthorized network devices, and retired or stale network segments.
Technology investments become more aligned and reduce costs associated with automation and digital transformation.

A weak vulnerability management program are a Hacker’s best friend

Security vulnerabilities grow faster than your team. That’s why you need our advisory service.

Configure and maintain application vulnerability scanning solutions to evaluate application vulnerabilities.

Create management plans and perform technical analysis to ensure that security vulnerabilities are mitigated.

Produce operational and tactical plans to remediate failed patch and secure configurations scan jobs, i.e., missing credentials, asset list updates, and firewall issues.

Perform false-positive analysis, remediation advice, vulnerability tracking through ticketing systems, and metrics development.

Conduct scheduled credential scan accounts, research, analyze vulnerabilities, identify relevant threats, provide corrective action recommendations, and communicate findings.

Serve as liaison between Security Assessment and Security Operation Center (SOC) functions on vulnerability scanning for security assessment efforts.

Research resolution for identified vulnerability findings and provide remediation and mitigation recommendations.

We utilize AI technologies to drive and automate trending analysis and data correlation for various security tools and intelligence platforms.







