Security Assessment & Authorization
We are experts at driving the SA&A process to support the Federal Information Security Modernization Act (FISMA) and DoD Readiness requirements.
Security Assessment & Authorization
We help clients gain security visibility and control into internal and external risks that impact the federal and DoD architects.
How We Can help
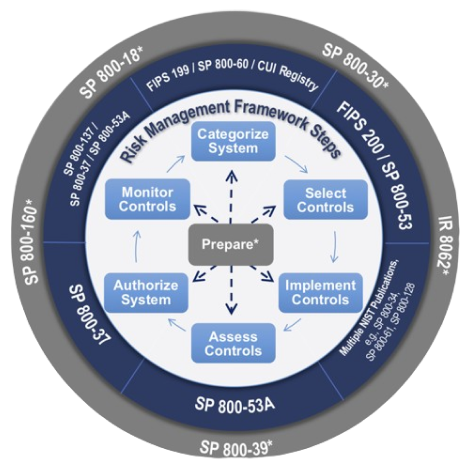
Road Mapping Cybersecurity
We help clients gain security visibility and control into internal and external risks that impact the federal and DoD architects. Our approach ensures that effective risk management programs create value and are tailored to system and agency's specifications; and engages cybersecurity as a continual improvement and enhancement
Driving Cybersecurity Outcomes
Our RMF Assessment and Authorization (A&A) process provides a structured, yet flexible approach for managing the portion of risk resulting from the incorporation of information systems into the mission and business processes of hte organization; and processes to help agencies pass FISMA, CCRI Inspections, and OIG Audits
Our value-added A&A Solutions
We embed our capabilities into the NIST RMF Process to support the DoD and Federal agencies’ requirements
- Real-time risk management and ongoing information system authorization through robust continuous monitoring processes.
- Automated process for selecting, implementing, assessing, and monitoring security controls, and authorizing information
- Integrated information security process into the enterprise architecture and system development life cycle
- Responsibility and accountability process for security controls deployed within organizational information systems and inherited (i.e., Common Controls) by those systems.
- Information to senior leadership needed for cost-effective, risk- based decisions regarding the organizational information systems supporting their core missions and business functions.
- Discovery of security deficiencies and event data that’s mapped to eMass and GRC tools.
- Real-time risk management and ongoing information system authorization through robust continuous monitoring processes.
- Automated process for selecting, implementing, assessing, and monitoring security controls, and authorizing information
- Integrated information security process into the enterprise architecture and system development life cycle
-
Responsibility and accountability process for security controls deployed within organizational information systems and inherited (i.e., Common Controls) by those systems.
Automated importand mapping capability for vulnerability assessment and system eventdata.
-
Information to senior leadership needed for cost-effective, risk- based decisions regarding the organizational information systems supporting their core missions and business functions.
Integrated information security process into the enterprise architecture and system development life cycle
- Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed nunc elit, mattis et lorem sit amet, eleifend rutrum erat. Vestibulum eu dui in sapien malesuada ornare eget et nunc. Suspendisse accumsan mi et bibendum volutpat. Nulla quis facilisis quam. Nulla facilisi.