The Battle Ahead Requires Decision Makers and An Arsenal of Cybersecurity Talent
Invest in talent to keep up with evolving skill demands and maintain your competitive edge. Use our workforce management capabilities to adapt quickly and excel.
Making A Difference
The workforce has undergone significant changes, with technologies like AI revolutionizing people’s work. Many laborers are concerned about the potential loss of their jobs. This is where reskilling and upskilling become essential.

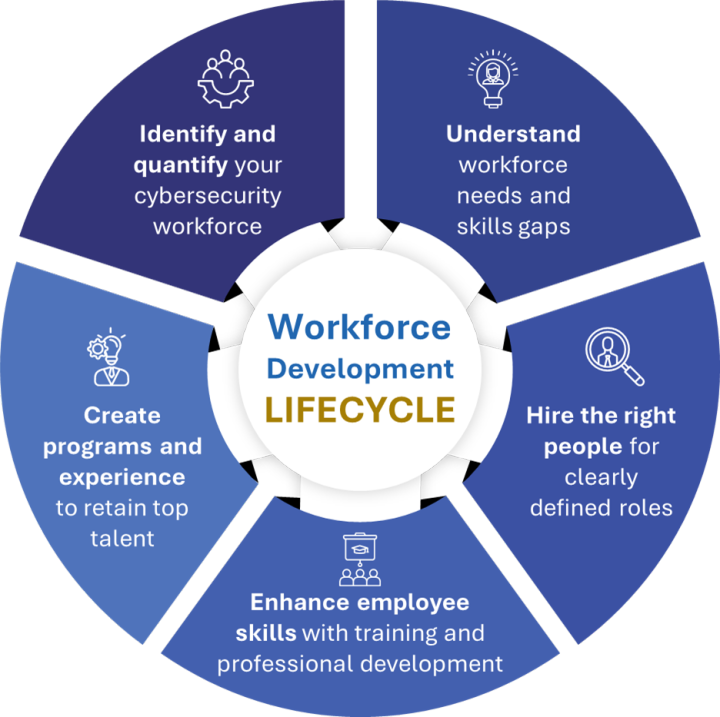
Key Aspects of Our Workforce Solutions
- Assess Skills: Evaluates current labor and training to support operations and modernization requirements.
- Talent Acquisition: Helps to streamline recruitment and labor assessment based on technical needs.
- Workforce Management Provides efficient means to optimize daily workloads, including tasks and roles.
- Risk Management: Advise on workforce risks associated with training, skillsets, and talent acquisition.
- Operational improvement: Identify key challenges and means to improve daily workforce engagements.
Assessing Workforce Programs
Harness talent for business success
We understand your strategy and anticipate changes in talent needs. By identifying key factors for success, we emphasize essential roles and skills, creating a flexible talent roadmap for today and the future.
Identify and close gaps
We identify skill gaps and develop strategies to fill them, ensuring the right talent is always available. By analyzing demand, organizations can proactively upskill or recruit to prevent performance disruptions.
Evaluate and stay competitive
Using proprietary data, we assess talent needs, benchmark against industry trends, and align workforce capabilities with future goals, helping companies adapt and maintain a competitive edge.
Workforce Analysis and Reporting (WAR) Service
Talent Acquisition
Staff alignment positions corporations to change working roles and tasks before they become critical.
Job Skill Analysis
helps organizations understand potential workforce issues, create targeted training programs, and make informed recruitment decisions.
Learning Development
Identify training and resources to provide required training based on labor categories and skillsets.
