Security and Risk Management
- Offering a comprehensive Security and Risk Management program for organizations to correlate risk to their security goals.
- Helping you manage risks effectively and in a balanced and holistic mindset.
- Providing a comprehensive evaluation of existing security landscape, best practices, and regulatory requirements.
We use security indicators to improve reporting, monitoring, and risk mitigation. These indicators enable clients to forecast operational tasks and identify risks or potential losses before their occurrence. We provide metrics and gap analysis by utilizing automated tools: eMass, RiskVision, CSAM, HBSS, IBM BigFix, Fortify, ACAS, Nessus, Splunk that enable 360 degrees of security visibility.

Continuous
Assessment
Supports compliance for ongoing assessment of security control effectiveness; and continuous assessments, reporting, and authorization of information systems monitoring.

Continuous
Authorization
Develop a Security Authorization and Assessments master project list that enables near-real-time risk management of information systems.

Continuous
Reporting
Top risk contributors by security controls and system components; Status of open POA&Ms or Corrective Action Plans.

Continuous
Visibility
Increase Situational Awareness; and provide trend in overall residual risk, broken down by inherited risk, accepted risk, and risk to be mitigated.
Risk Management Solutions
Continuous Diagnostics & Mitigation (CDM) Program
Federal Information Security Modernization Act of 2014 (FISMA 2014)
Federal Risk and Authorization Management Program (FedRAMP)
RMF
Assessment
and Authorization
(A&A)
Federal Security Control Assessment (SCA) and Auditing
Security Analytics and Reporting (SA&R)
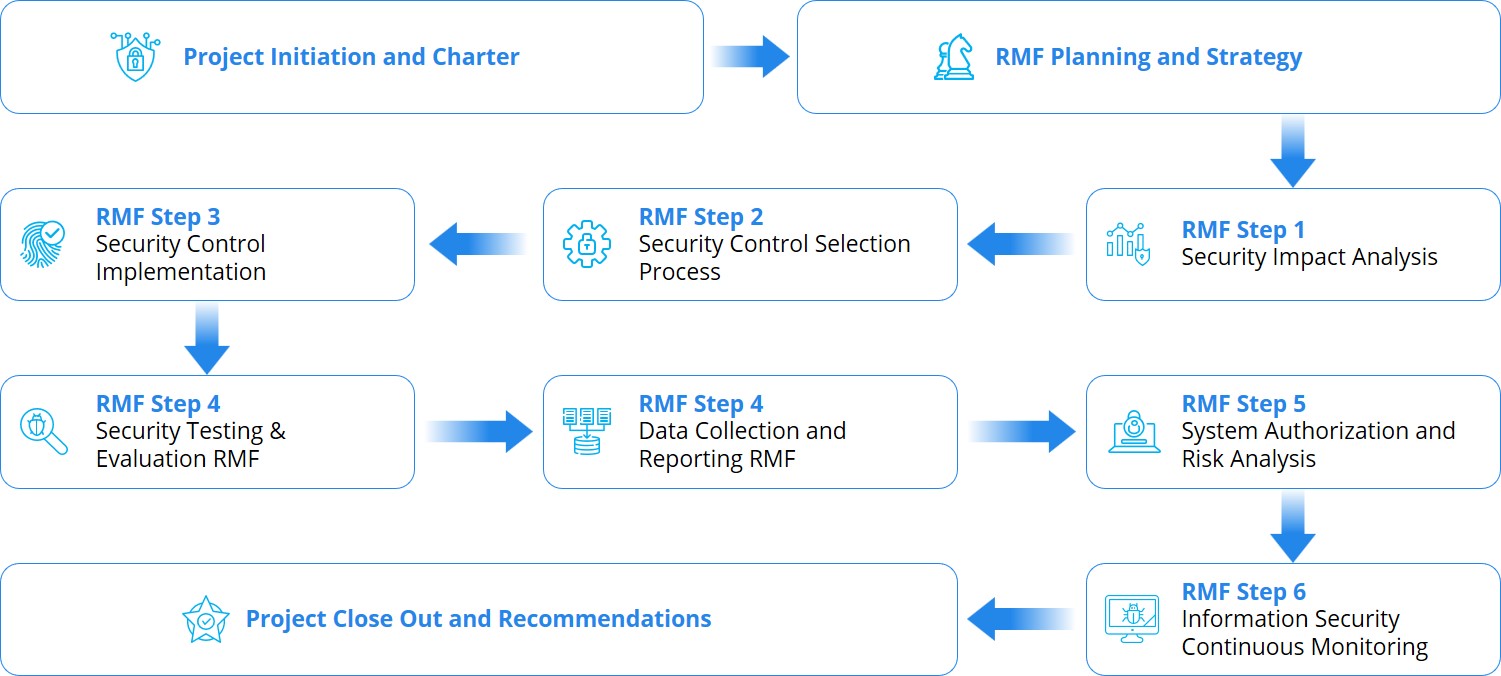
The Risk Management Framework (RMF) was developed by the National Institute for Standards and Technology (NIST) to help DoD and Federal agencies manage risks to and form Information Technology (IT) systems more easily, efficiently and effectively. The RMF Assessment and Authorization (A&A) process provides a structured, yet flexible approach for managing the portion of risk resulting from the incorporation of information systems into the mission and business processes of the organization; and processes to help agencies pass FISMA, CCRI Inspections, and OIG Audits. Through an Assessment and Authorization (A&A) systems can become secure and reliable.
Provides Key Reliabilities
Real-time risk management and ongoing information system authorization through the implementation of robust continuous monitoring processes.

Automated process for selecting, implementing, assessing, and monitoring security controls, and authorizing information systems.

Information to senior leadership needed for cost-effective, risk-based decisions regarding the organizational information systems supporting their core missions and business functions.
Responsibility and accountability process for security controls deployed within organizational information systems and inherited (i.e., Common Controls) by those systems.

Integrated information security process into the enterprise architecture and system development life cycle.

Automated import and mapping capability for vulnerability assessment and system event data.

Accurate Security Authorization Packages through the standardization of A&A process and documentation.