Enterprise Security
Our enterprise solutions validate readiness and the entire operational environment to optimize and maintain the security architecture.
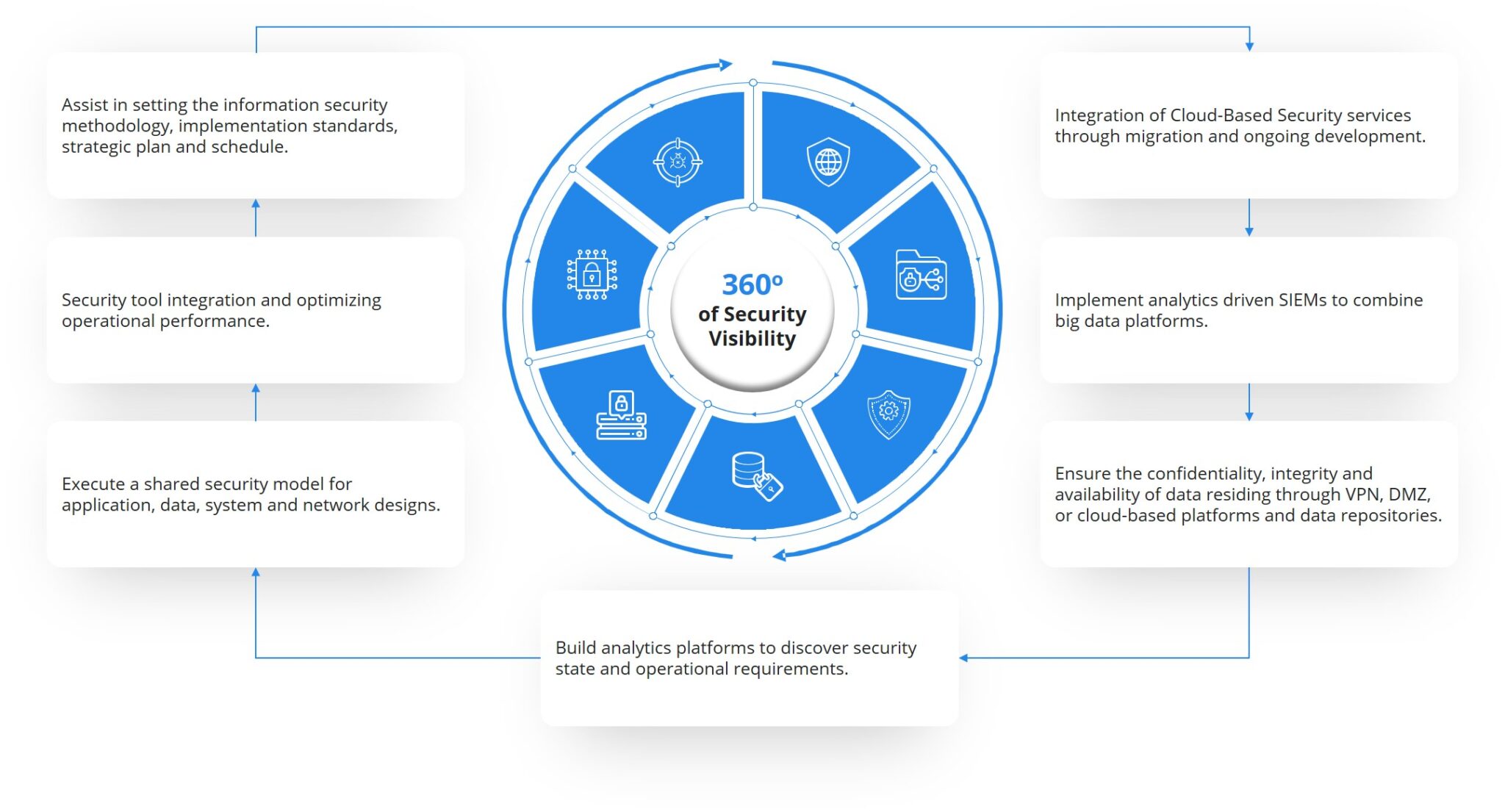
As organizations transform and digitally modernize, their security state of readiness must continuously evolve through an ongoing, collaborative effort between business and technology. The maturity of the Enterprise Architect (EA) reflects the varying states of governance, decision processes, integration, and standardization across the enterprise. We deliver a centralized security management structure to keep visible content secure within a client’s enterprise security model. Reducing enterprise risks is our business.

Business
Process and use

Data
Which must be sorted, organized, protected and distributed through

Application
Of custom or mass produced software tools managed by

Technology
Such as computer systems or telephone networks

Application Security Services
Application security addresses the design, development, validation, and usage of applications. With the wide disperse of web-based programs and industry risks, you need a solution provider that can operate within the fabric of application security. We can secure your applications by performing web-app assessments and secure code reviews.

Access Authorization and Identity Management Service
Knowing who, what, and when should employees gain privileged access requires various identity and access management solutions. We can articulate and drive identity integration and employee access through Common Access Card (CAC), Personal Identity Verification (PIV), or other industry-based solutions. Our solutions can architect and navigate your access authorization and identity management requirements.

Data Security Services
As organizations onboard different data points, privacy standards, electronic public health information (ePHI), and cloud-based initiatives, protecting data becomes critical. Knowing where data resides and protecting the repository reduces legal issues and instills public confidence. This is where Semais expertise and data protection solutions operate.

Endpoint Services
Service connection desktops, mobile devices, kiosks, or other endpoint is challenging. Configuring devices and assigning visibility rights requires system-wide consideration. A defect in endpoint security can cause malware, data loss, false-positive analysis, or undiscovered assets. We can install agents and configure your endpoints to sustain 360-degree compliance and visibility success.